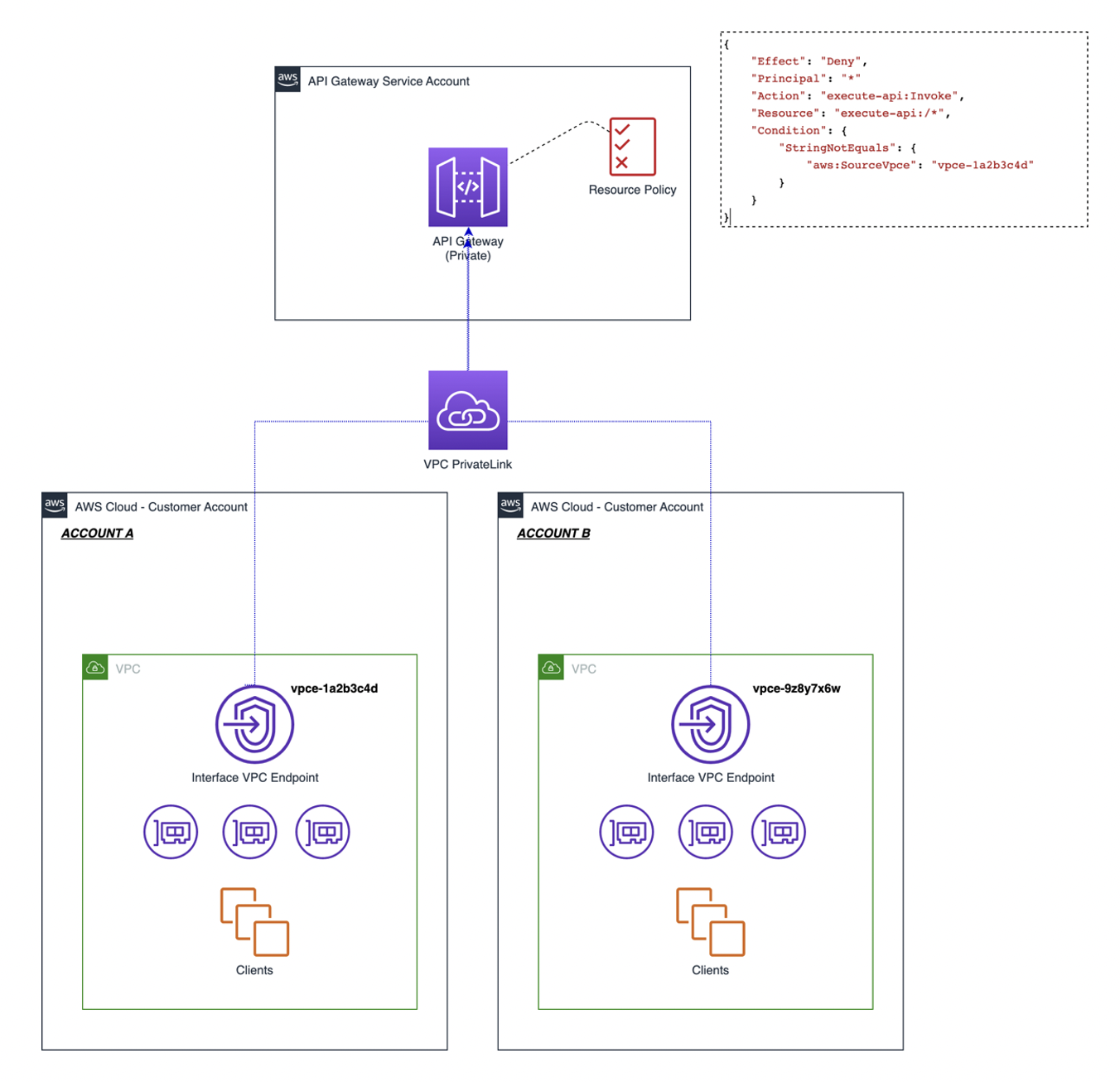
How can I access an API Gateway private REST API in another AWS account using an interface VPC endpoint¶
topo¶
In Account A¶
- create vpc &
execute-apiendpoint - no peering or tgw needed
In API gateway Service Account¶
access-control-with-cidr¶
- works.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Deny", "Principal": "*", "Action": "execute-api:Invoke", "Resource": "execute-api:/*/*/*", "Condition": { "NotIpAddress": { "aws:SourceIp": "10.251.0.0/16" } } }, { "Effect": "Allow", "Principal": "*", "Action": "execute-api:Invoke", "Resource": "execute-api:/*/*/*" } ] }
access-control-with-vpce¶
- works.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Deny", "Principal": "*", "Action": "execute-api:Invoke", "Resource": "execute-api:/*/*/*", "Condition": { "StringNotEquals": { "aws:sourceVpce": ["vpce-0e8c7xxb45","vpce-05d2xx259"] } } }, { "Effect": "Allow", "Principal": "*", "Action": "execute-api:Invoke", "Resource": "execute-api:/*/*/*" } ] }
access-control-with-vpc¶
- works
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Deny", "Principal": "*", "Action": "execute-api:Invoke", "Resource": "execute-api:/*/*/*", "Condition": { "StringNotEquals": { "aws:sourceVpc": "vpc-0204axxx0" } } }, { "Effect": "Allow", "Principal": "*", "Action": "execute-api:Invoke", "Resource": "execute-api:/*/*/*" } ] }
deploy¶
- redeploy after you change
Resource Policy