eksctl-cmd¶
install¶
# install eksctl
# consider install eksctl version 0.89.0
# if you have older version yaml
# https://eksctl.io/announcements/nodegroup-override-announcement/
curl --location "https://github.com/weaveworks/eksctl/releases/latest/download/eksctl_$(uname -s)_amd64.tar.gz" | tar xz -C /tmp
sudo mv -v /tmp/eksctl /usr/local/bin
eksctl completion bash >> ~/.bash_completion
. /etc/profile.d/bash_completion.sh
. ~/.bash_completion
refer: ../../cloud9/setup-cloud9-for-eks
auto-mode-¶
oidc-¶
eksctl utils associate-iam-oidc-provider --cluster $CLUSTER_NAME --region $AWS_DEFAULT_REGION --approve
iamidentitymapping-¶
- add role to
aws-authconfigmap (eks-aws-auth)
create windows self-managed node group¶
CLUSTER_NAME=myeksctl
export AWS_DEFAULT_REGION=us-west-2
eksctl create nodegroup \
--cluster $CLUSTER_NAME \
--name nodegroup-win-1 \
--node-type m5.xlarge \
--nodes 1 \
--nodes-min 1 \
--nodes-max 2 \
--node-ami-family WindowsServer2019FullContainer \
--managed=false
CLUSTER_NAME=myeksctl
export AWS_DEFAULT_REGION=us-west-2
eksctl create nodegroup \
--cluster $CLUSTER_NAME \
--name nodegroup-br-1 \
--node-type m5.xlarge \
--nodes 1 \
--nodes-min 1 \
--nodes-max 2 \
--node-ami-family Bottlerocket
create nodegroup¶
- create nodegroup on a cluster which not created by eksctl
scale nodegroup¶
CLUSTER_NAME=ekscluster1
NODEGROUP_NAME=managed-ng
AWS_REGION=us-east-2
eksctl scale nodegroup \
--cluster=${CLUSTER_NAME} \
--region ${AWS_REGION} \
--nodes=3 \
${NODEGROUP_NAME}
func-create-iamserviceaccount-¶
eksctl create iamserviceaccount -c ekscluster1 \
--name sa-s3 --namespace default \
--attach-policy-arn arn:aws:iam::aws:policy/AmazonS3FullAccess \
--role-name sa-s3-$(TZ=EAT-8 date +%Y%m%d-%H%M%S) --approve \
--override-existing-serviceaccounts
appmesh cluster¶
eksctl create cluster \
--name appmeshtest \
--nodes-min 2 \
--nodes-max 3 \
--nodes 2 \
--auto-kubeconfig \
--full-ecr-access \
--appmesh-access
appmesh-access-¶
--appmesh-access will apply customer inline policy for appmesh
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"servicediscovery:CreateService",
"servicediscovery:DeleteService",
"servicediscovery:GetService",
"servicediscovery:GetInstance",
"servicediscovery:RegisterInstance",
"servicediscovery:DeregisterInstance",
"servicediscovery:ListInstances",
"servicediscovery:ListNamespaces",
"servicediscovery:ListServices",
"servicediscovery:GetInstancesHealthStatus",
"servicediscovery:UpdateInstanceCustomHealthStatus",
"servicediscovery:GetOperation",
"route53:GetHealthCheck",
"route53:CreateHealthCheck",
"route53:UpdateHealthCheck",
"route53:ChangeResourceRecordSets",
"route53:DeleteHealthCheck",
"appmesh:*"
],
"Resource": "*",
"Effect": "Allow"
}
]
}
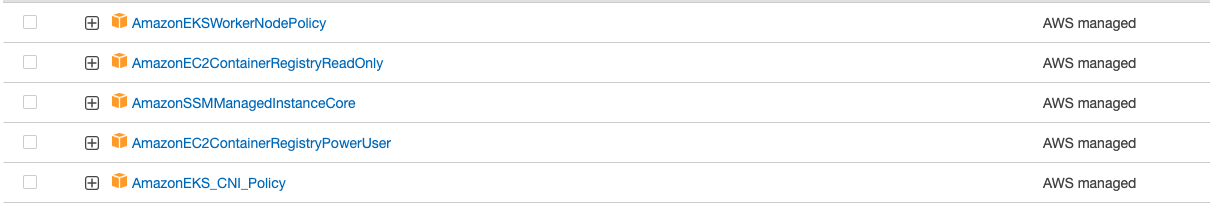
full-ecr-access¶
--full-ecr-access will apply ECR power user policy to node