Using Global SSO to Login China AWS Accounts¶
使用 global sso 登录中国区 aws 账号,同时实现使用命令行操作。
walkthrough¶
use identity center directory as identity source¶
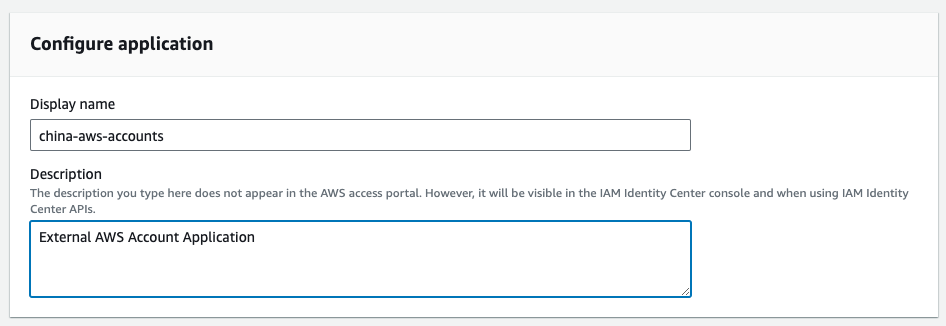
- create application
External AWS Account Applicationfrom ssoApplications
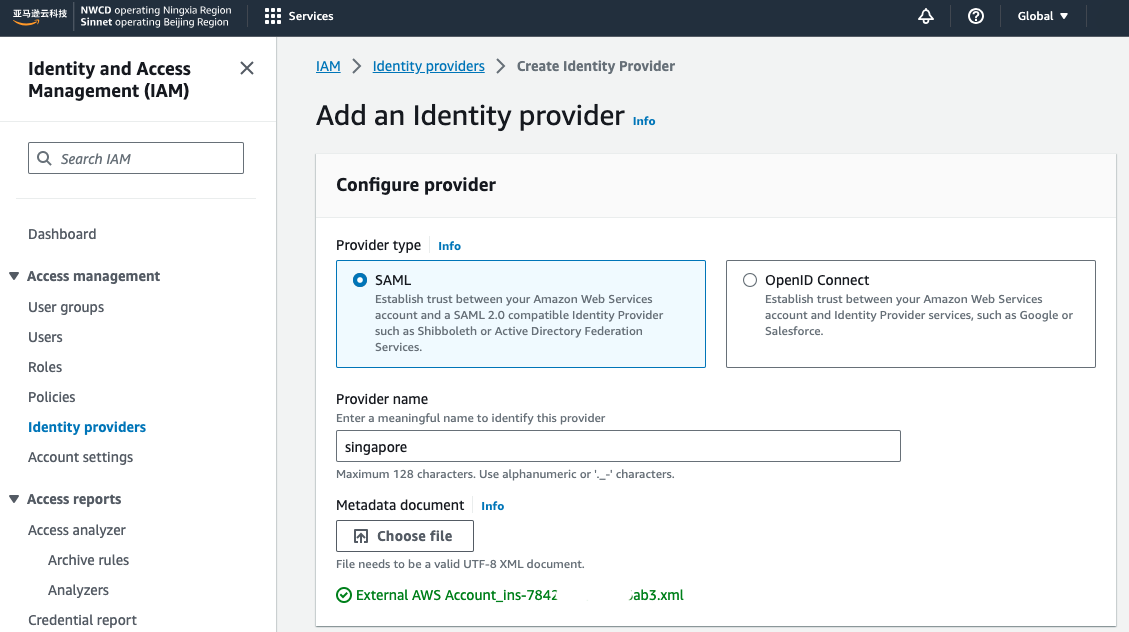
-
download
IAM Identity Center SAML metadata file -
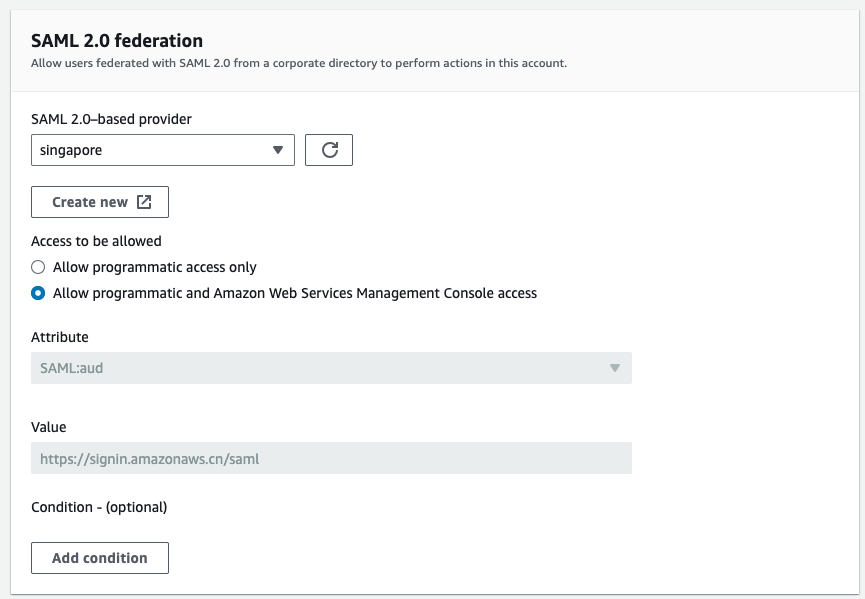
create role for
SAML 2.0 federationin aws china account, and assign policy to it
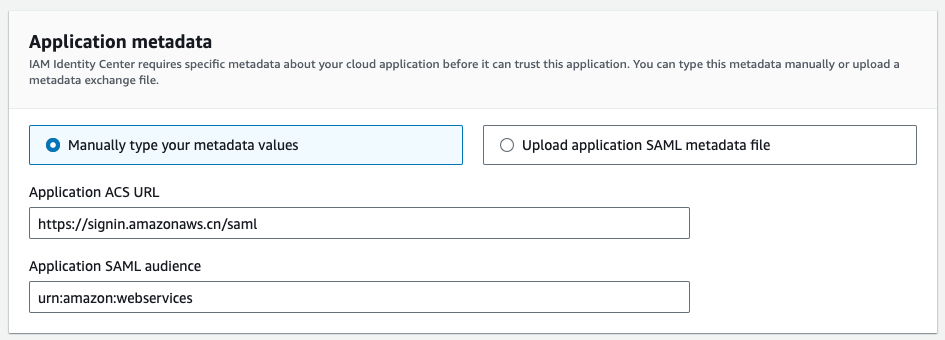
-
back to create application page, review application metadata
-
create application
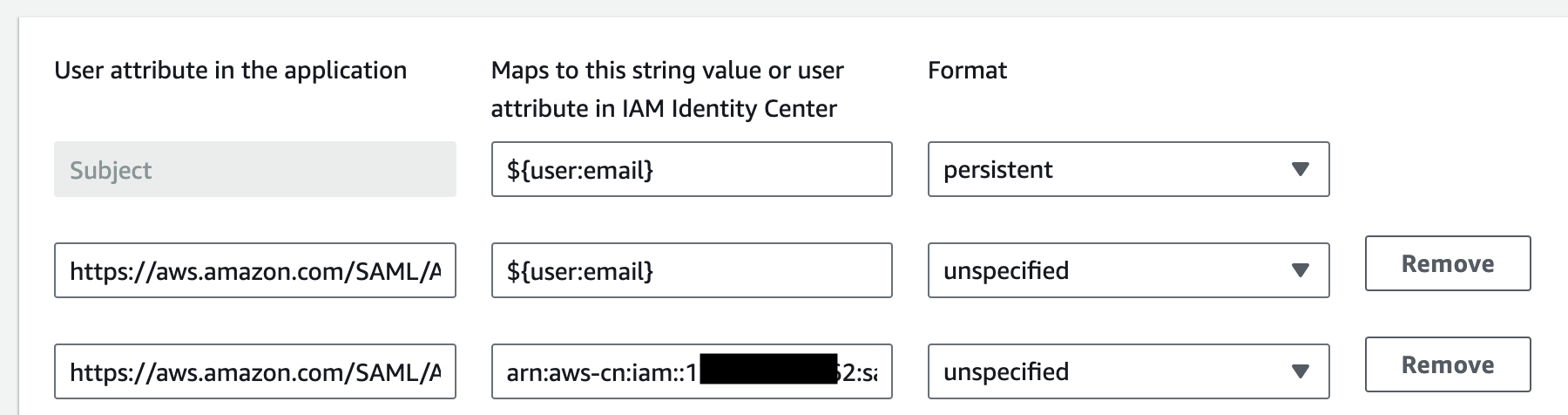
- edit
attribute mappingsfor this application, ensure following two field existed
| Field | Value | Format |
|---|---|---|
https://aws.amazon.com/SAML/Attributes/Role |
arn:aws:iam::ACCOUNTID:saml-provider/SAMLPROVIDERNAME,arn:aws:iam::ACCOUNTID:role/ROLENAME | unspecified |
https://aws.amazon.com/SAML/Attributes/RoleSessionName |
unspecified |
use managed AD as identity source¶
use external IdP as identity source¶
- todo
in same organization user and role¶
- in multi-account permissions, choose account, and assign user/group to it, assign permission set to it.
- assume from CLI